Create Locally-Managed Cloudflare Tunnel
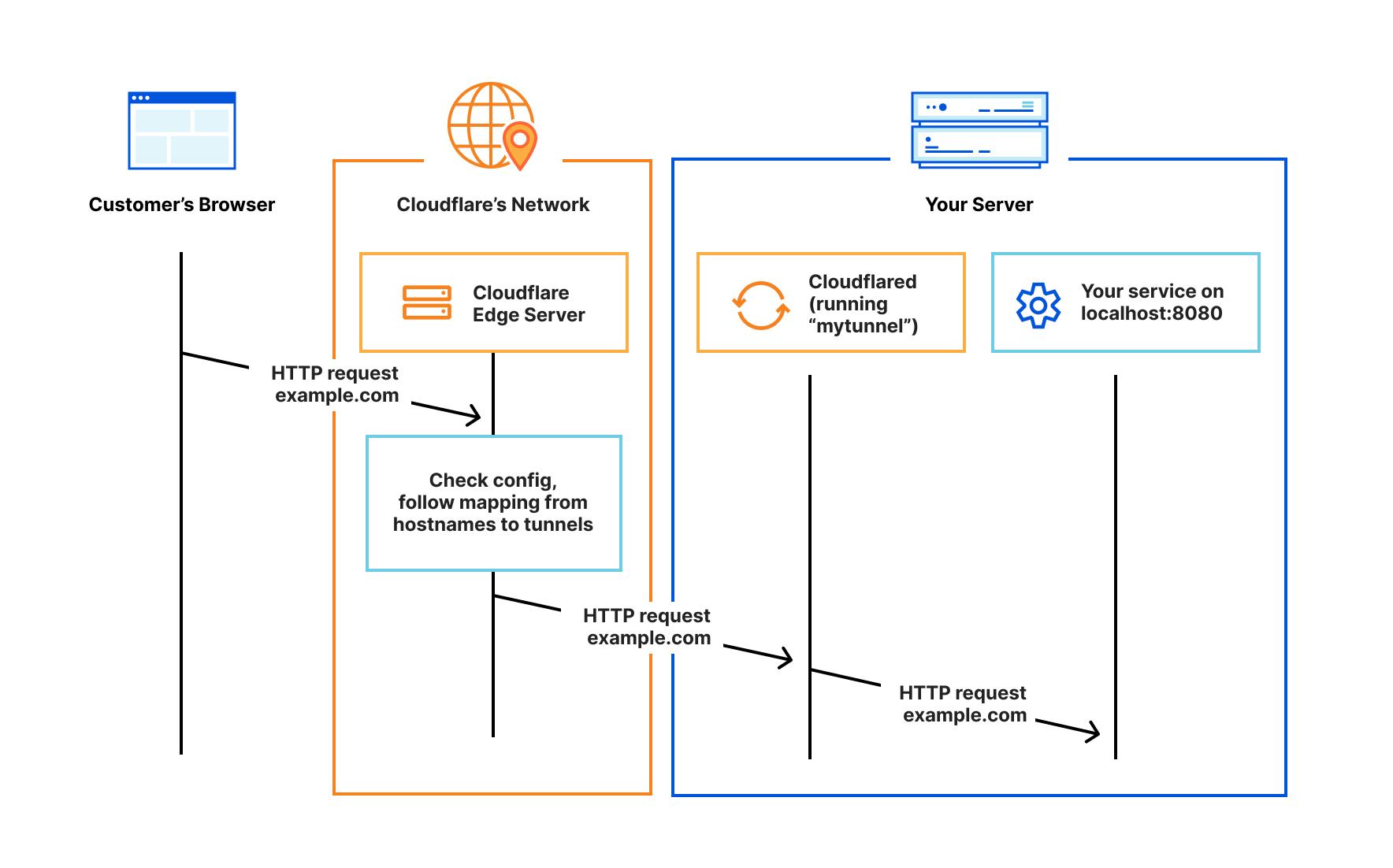
Cloudflare Tunnel provides you with a secure way to connect your resources to Cloudflare without a publicly routable IP address. With Tunnel, you do not send traffic to an external IP — instead, a lightweight daemon in your infrastructure (cloudflared) creates outbound-only connections to Cloudflare’s global network. Cloudflare Tunnel can connect HTTP web servers, SSH servers, remote desktops, and other protocols safely to Cloudflare. This way, your origins can serve traffic through Cloudflare without being vulnerable to attacks that bypass Cloudflare.
How it works
Cloudflared establishes outbound connections (tunnels) between your resources and Cloudflare’s global network. Tunnels are persistent objects that route traffic to DNS records. Within the same tunnel, you can run as many cloudflared processes (connectors) as needed. These processes will establish connections to Cloudflare and send traffic to the nearest Cloudflare data center.
Prerequisites
Before you start, make sure you:
1. Install cloudflared
Windows
- Download cloudflared on your machine. Visit the downloads page to find the right package for your OS.
- Rename the executable to cloudflared.exe
- In PowerShell, change directory to your Downloads folder and run
.\cloudflared.exe --version. It should output the version ofcloudflared. Note thatcloudflared.execould becloudflared-windows-amd64.exeorcloudflared-windows-386.exeif you have not renamed it.
|
|
macOS
To download and install cloudflared:
|
|
Alternatively, you can download the latest Darwin amd64 release directly.
Linux
Debian and Ubuntu APT
Use the apt package manager to install cloudflared on compatible machines.
- Add Cloudflare’s package signing key:
|
|
- Add Cloudflare’s apt repo to your apt repositories:
|
|
- Update repositories and install cloudflared:
|
|
RHEL RPM
Use the rpm package manager to install cloudflared on compatible machines.
- Add Cloudflare’s repository:
|
|
- Update repositories and install cloudflared:
|
|
Arch Linux
cloudflared is in the Arch Linux community repository. Use pacman to install cloudflared on compatible machines.
|
|
Other
Alternatively you can download the cloudflared binary or the linux packages to your machine and install manually. Visit the downloads page to find the right package for your OS.
Build from source
To build the latest version of cloudflared from source:
|
|
Depending on where you installed cloudflared, you can move it to a known path as well.
|
|
2. Authenticate cloudflared
|
|
Running this command will:
- Open a browser window and prompt you to log in to your Cloudflare account. After logging in to your account, select your hostname.
- Generate an account certificate, the cert.pem file, in the default cloudflared directory.
3. Creae a tunnel and give it a name
|
|
Running this command will:
- Create a tunnel by establishing a persistent relationship between the name you provide and a UUID for your tunnel. At this point, no connection is active within the tunnel yet.
- Generate a tunnel credentials file in the default cloudflared directory.
- Create a subdomain of
.cfargotunnel.com.
From the output of the command, take note of the tunnel’s UUID and the path to your tunnel’s credentials file.
Confirm that the tunnel has been successfully created by running:
|
|
4. Create a configuration file
-
In your
.cloudflareddirectory, create a config.yml file using any text editor. This file will configure the tunnel to route traffic from a given origin to the hostname of your choice. -
Add the following fields to the file:
If you are connecting an application:
|
|
If you are connecting a private network:
|
|
- Confirm that the configuration file has been successfully created by running:
|
|
5. Start routing traffic
-
Now assign a
CNAMErecord that points traffic to your tunnel subdomain:- If you are connecting an application, route the service to a public hostname:
1$ cloudflared tunnel route dns <UUID or NAME> <hostname>- If you are connecting a private network, route an IP address or CIDR through the tunnel:
1$ cloudflared tunnel route ip add <IP/CIDR> <UUID or NAME> -
Confirm that the route has been successfully established:
1$ cloudflared tunnel route ip show
6. Run the tunnel
Run the tunnel to proxy incoming traffic from the tunnel to any number of services running locally on your origin.
|
|
If your configuration file has a custom name or is not in the .cloudflared directory, add the --config flag and specify the path.
|
|
Cloudflare Tunnel can install itself as a system service on Linux and Windows and as a launch agent on macOS. For more information, refer to run as a service.
7. Check the tunnel
Your tunnel configuration is complete! If you want to get information on the tunnel you just created, you can run:
|
|
You can now route traffic to your tunnel using Cloudflare DNS or determine who can reach your tunnel with Cloudflare Access.
Useful commands
Use these commands to manage local tunnels through the CLI.
Manage tunnels
| Command | Description |
|---|---|
cloudflared tunnel login |
Prompts a browser window where you can authenticate your tunnel to your Cloudflare account. |
cloudflared tunnel list |
Displays all active tunnels, their creation time, and associated connections. Use the -d flag to include deleted tunnels. |
cloudflared tunnel create <NAME or UUID> |
Creates a tunnel, registers it with the Cloudflare edge and generates a credential file to run this tunnel. |
cloudflared tunnel route |
Routes traffic through a tunnel. |
cloudflared tunnel route lb <NAME or UUID> <load balancer name> <load balancer pool> |
Creates a Load Balancer with an origin pool that points to the tunnel. |
cloudflared tunnel route ip add <IP/CIDR> <NAME or UUID> |
Adds any network route space (represented as a CIDR) to your routing table. That network space becomes reachable for requests egressing from a user’s machine as long as it is using Cloudflare WARP and is enrolled in the same account that is running the tunnel chosen here. Further, those requests will be proxied to the specified tunnel, and reach an IP in the given CIDR, as long as that IP is reachable from the tunnel. To assign the IP route to a specific Virtual Network, use the --vnet option. |
cloudflared tunnel route ip show (or list) |
Shows your organization’s private routing table. You can use additional flags to filter the results. |
cloudflared tunnel route ip delete |
Deletes the row for a given CIDR from your routing table. That portion of your network will no longer be reachable by the WARP client. |
cloudflared tunnel route ip get <IP/CIDR> |
Checks which row of the routing table will be used to proxy a given IP. This helps check and validate your configuration. |
cloudflared tunnel route dns |
Creates a DNS CNAME record hostname that points to the tunnel. |
cloudflared tunnel --config path/config.yaml run <NAME or UUID> |
Runs a tunnel, creating highly available connections between your server and the Cloudflare edge. You can provide name or UUID of the tunnel to run either as the last command line argument or in the configuration file using tunnel: <NAME>. |
cloudflared tunnel info <NAME or UUID> |
Displays details about the active connectors for a given tunnel identified by name of UUID. |
cloudflared tunnel cleanup <NAME or UUID> |
Deletes connections for tunnels with the given UUIDs or names. This is useful if you get an error trying to delete or run a tunnel after cloudflared is not shut down gracefully (for example, if a kill command is issued). |
cloudflared tunnel cleanup --connector-id <CONNECTOR-ID> <NAME or UUID> |
Disconnects and deletes a cloudflared replica with the given connector ID. You can view all replicas for a tunnel by running cloudflared tunnel info <NAME or UUID>. |
cloudflared tunnel delete <NAME or UUID> |
Deletes tunnels with the given name or UUID. A tunnel cannot be deleted if it has active connections. To delete the tunnel unconditionally, use the -f flag. |
cloudflared tunnel vnet add <NAME or UUID> |
Creates a Virtual Network to which IP routes can be assigned. To make this Virtual Network the default for your Zero Trust organization, use the -d flag. |
cloudflared tunnel vnet delete <NAME or UUID> |
Deletes the Virtual Network with the given name or UUID. Before you can delete a Virtual Network, you must first delete all IP routes assigned to the Virtual Network. |
cloudflared tunnel vnet list |
Displays all active Virtual Networks, the default Virtual Network, and their creation times. |
cloudflared tail <UUID> |
Start a session to livestream logs from a specific tunnel. For more information, refer to Tunnel logs. |
Manage cloudflared
| Command | Description |
|---|---|
cloudflared update |
Looks for a new version on the official download server. If a new version exists, it updates the agent binary and quits. Otherwise, no action is performed. This command only works if cloudflared was installed from GitHub binaries or from source. For more information, refer to the update instructions. |
cloudflared version |
Prints the cloudflared version number and build date. |
cloudflared help |
Shows a list of commands or help for cloudflared. |